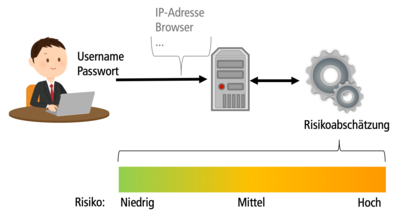
With the RBA authentication method (risk-based authentication), an online service only accepts a user name and password as long as it does not detect any anomalies. If RBA is not sure whether the legitimate user wants to log in due to behavior or situational circumstances, it asks for additional authentication.
RBA is still used almost exclusively by large U.S. online services such as Amazon, Facebook, Google, and LinkedIn. Nevertheless, a new long-term study by a team of researchers at the Horst Görtz Institute for IT Security and the Bonn-Rhein-Sieg University of Applied Sciences proves that the method is not only more user-friendly than comparable 2FA methods but also achieves a high level of security.
For the study, Stephan Wiefling, Markus Dürmuth, and Luigi Lo Iacono observed the user behavior of 780 users on an online service for almost two years. They examined two RBA algorithms used in practice for their security and usability properties in this real-world context.
Rarely asks for additional authentification
Their results show that RBA very rarely asks for additional authentication in practice. This remains valid even if more than 99.45% of intelligent attacks are blocked, according to the researchers - referring to attacks with knowledge of the victim's credentials, as well as their typical location (city, country), browser, and device. The researchers also revealed that only a few characteristics are useful for the authentication method. In other words, online services do not need to collect many of these characteristics to achieve good RBA security and usability. As a result, the researchers are introducing for the first time a measure that can be used to evaluate the data sparseness and purposefulness of RBA features from a privacy perspective. In their work, the team also developed a new feature that detects known attacks on RBA and further increases the cost to attackers.
RBA protects against attacks using stolen login credentials, such as phishing or credential stuffing. Despite the increased usability and security gains at hand, however, only a few small and medium-sized websites use the technology, even though it is recommended by authorities such as the National Institute of Standards and Technology (NIST, USA) and the National Cyber Security Centre (NCSC, UK). The researchers assume this is due to the lack of knowledge about RBA and the associated difficulties in implementation. The research team's scientific work provides valuable insights in this regard, which should promote wider use.
Discussions on RBA as an security solution
To achieve greater visibility of RBA as an effective and immediate hardening of password-based authentication systems in Germany, the researchers would like to see more discussions on RBA as an security solution that plays a significant role on the road to a passwordless future. In the view of the security researchers, leaving password-based authentication systems in use in their current state and disregarding RBA while waiting for widespread deployment of multifactor authentication is irresponsible.
The paper will be presented at this year's "Financial Cryptography and Data Security" conference in March. The technical details and downloadable paper can be found here.
Press contact
Stephan Wiefling
Data and Application Security Group
Hochschule Bonn-Rhein-Sieg
Tel.: +49 2241 865 9567
Web: https://das.h-brs.de
Mail: stephan.wiefling(at)h-brs.de
General note: In case of using gender-assigning attributes we include all those who consider themselves in this gender regardless of their own biological sex.