With their millions of conductor tracks and transistors, electronic microchips are almost reminiscent of futuristic metropolises with a complex network of streets stretching over several floors. Nowadays, however, they are often so small that the individual roads and buildings cannot be seen with the naked eye. The miniature landscapes ensure that the electronics in modern cars work, that the refrigerator can be controlled with a mobile phone or that automated production processes run in industry. Microchips have become indispensable.
The development of such a component can cost several million euros. So the temptation is great in some places not to think up the electronics landscape from scratch, but to look at what the competition already has. So-called hardware reverse engineering helps to steal ideas. Cognitive researcher Dr. Carina Wiesen and IT security researcher Dr. Steffen Becker are interested in how people go about this. The two researchers have completed their PhD at the RUB as research tandem in the SecHuman research college on the topic. Why it is a tough business to investigate hardware reverse engineering, the two tell in the interview.
Building a chip backwards to steal the design plan sounds costly. Is that really cheaper than developing the technology yourself?
Steffen Becker: Actually, yes, at least when it comes to bread-and-butter chips that are installed millions of times over, not the latest high-tech products from Apple or Intel. If you steal the design plan for a chip, you save the costs for research and development, don't have to do your own marketing and don't have to worry about drivers.
And how does hardware reverse engineering work?
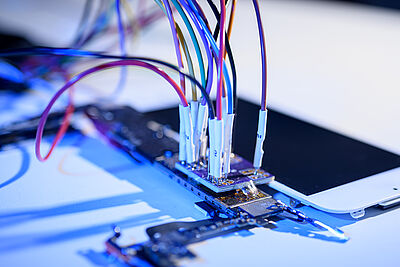
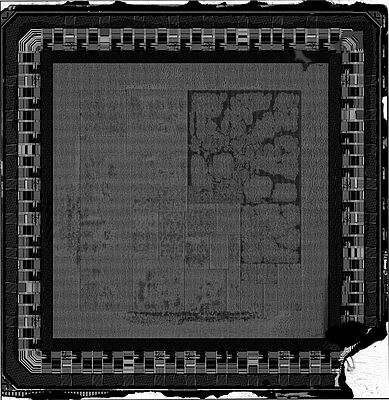
Becker: Full-scale reverse engineering is costly. A chip with an area of one square millimetre can have several hundred thousand gates on it. The chip is three-dimensional and consists of up to 20 layers. First, you make a cross-section of the chip to see how many layers it has, how thick it is and what materials it contains. Then each individual layer is removed in turn using chemical processes and images of each exposed layer are taken with an electron scanning microscope – several hundred or several thousand images per layer. Finally, these are combined to form a three-dimensional image
You can do all this with a single chip?
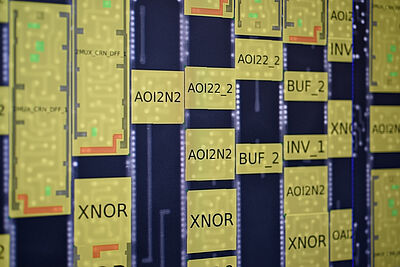
Becker: No, you need several dozen chips because you break them in the process. It's also not as simple as it sounds at first. A lot can go wrong in the process; you need a lot of experience to even begin to get it right. Once you have created the three-dimensional image of the chip, you can generate the so-called netlist from it. It includes all the digital circuits consisting of the logical gates and memory elements with their connections. However, the netlist is not yet a finished construction plan; if you want to rebuild a chip, you have to analyse it. However, the goal is not always to understand the complete netlist – that would be the holy grail. Sometimes it is enough to find and understand important subcomponents.
Hardly anyone has looked at the human analysis processes before us.
– Carina Wiesen
At first, that sounds like just a technical process. But in your interdisciplinary research you also shed light on a psychological component.
Carina Wiesen: Hardware reverse engineering is an opaque process that is not well understood. As a rule, sub-processes run automatically. But then humans have to make sense of the result. Hardly anyone has looked at these human analysis processes before us. Understanding the netlist – that can be defined as a big problem that can be solved using different strategies. We want to find out which strategies people use to do this, and we apply psychological models from the problem-solving field. To do this, we first had to develop a method – that took three or four years.
What is the goal of this research?
Wiesen: It's about being able to better protect intellectual property. If we know how people reverse engineer hardware, we might be able to develop protective measures that make it harder to use the usual problem-solving strategies.
Do people ever notice when ideas are stolen through hardware reverse engineering? And is the theft punished?
Becker: Reverse engineering is generally permitted in the USA, for example: The main point here is that compatibility can be established with devices from other manufacturers. Ultimately, however, it is always a legal balancing act between laws on patent and copyright protection on the one hand and trade and consumer protection laws on the other.
Behind closed doors, a real battle for the patents is raging.
– Steffen Becker
Only a few cases of idea theft through reverse engineering are publicly known. Behind closed doors, however, a real battle rages over patents and the respective intellectual property, in which the big competitors examine each other's hardware for intellectual property theft. If they find possible infringements, however, they usually take the discreet legal route, and technical details are only made public in the rarest of cases.
Can hardware reverse engineering actually be used for other purposes – or only to steal know-how?
Becker: The criminal side is only one side of the coin. For example, reverse engineering can also help to find manipulations of hardware.
How can this process be researched at all? Idea thieves are hardly going to let you look over their shoulder as they work.
Wiesen: There are only a few experts in hardware reverse engineering. So we asked ourselves: How can we observe people while they analyse unknown netlists? Steffen developed a course for students of IT security, computer science and electrical engineering, who were introduced to hardware reverse engineering for six months. At the end of this course, they had to analyse parts of a netlist. In the process, log files were recorded from which we could subsequently deduce how they had proceeded.
Becker: We have now held the course six times, once also in the USA. It is helpful for us to have contact with experts from security authorities or from industry. They give us feedback on whether we are using the right attacker models in our course and analysing the right problems. So far, that seems to be the case.
Are there already results from the course?
Wiesen: We have seen, for one thing, that the students were similarly fast as experts in analyzing the netlists after the course. There was overlap in the strategies used, but nevertheless everyone does it somehow in their own way. We also surveyed the IQ of the participants and tested their working memory capacity. The result was that people with a better working memory were also better at understanding the netlists. So you could try to design protective measures to overload the working memory in hardware reverse engineering.
Meanwhile, you came up with something else new to increase your sample size.
Wiesen: Yes, we have developed an online game that maps individual processes of reverse engineering. Anyone should be able to play it without prior knowledge. This way we hope to get more data. The first pilot tests have been successful.
With the game we want to find out what makes reverse engineering difficult.
– Steffen Becker
Becker: With the game, we want to find out what makes reverse engineering difficult. From this we can deduce what hardware components must look like so that the circuits are less easy to understand. We can then incorporate these new ideas into real netlists, but also back into the game as tasks and see if they have become more difficult to solve.
You have to be very creative to get your data. Did you ever worry that the methodological problems would get in the way of your work?
Wiesen: It was and is a very interesting and fun project. But because it is so new, we had problems publishing on it. We had to fight our way through. But in the end we managed to get a good publication and another article is currently in the review process.
Becker: Another problem is that much of this research takes place in the context of national security. Experts are employed directly by the military or intelligence services to work on reverse engineering – and then nothing of the results gets out to the public. Nevertheless, we see that something has developed from our research in the meantime. The amount of supervision required for our studies is very high, but it is definitely worth it.
About SecHuman
In the research college "SecHuman - Security for People in Cyberspace", doctoral students examine technical and social problems of IT security in interdisciplinary cooperation. Within this framework, Carina Wiesen from the Department of Educational Psychology at the Institute of Educational Science (Prof. Dr. Nikol Rummel) and Steffen Becker from the Horst Görtz Institute for IT Security (Prof. Dr. Christof Paar) completed a tandem doctorate.
Author: Julia Weiler
General note: In case of using gender-assigning attributes we include all those who consider themselves in this gender regardless of their own biological sex.